Lesson 24 - Layer 2 Etherchannel
Lesson 24 - Layer 2 Etherchannel
There are two more things I would like to cover in this Cisco fundamentals series that relates to switches: the etherchannel technology and switch port security. Then we move on to layer 3 stuff.
Layer 2 Etherchannel
When you're designing your network one of the factors you always consider is resiliency. Redundant connections are part of a good design. Consider picture 1 below. A rule of thumb says that if all the devices connected to SW3(access switch on first floor) were transmitting at full speed towards distribution switches (here towards SW1) the traffic is allowed to exceed the capacity of F0/2 port on SW1 20 times. In other words, the link between access layer could oversubscribe 20:1 the link on the distribution switch. Well, it is true in most cases. Remember this is just a rule for an average network.
In reality, the situation in which all computers begin to transmit at full speed at the same time never happens. The studies show, that the link between access and distribution switch is utilized in 7% on the average (unless some worm has been planted on your computers). In order to live up to this rule (oversubscription 20:1) you might consider access-to-distribution connection using multiple links that form a virtual connection called: etherchannel. Ports that are members of the etherchannel are represented by a virtual interface called: port-channel.
Etherchannel Advantages
Etherchannel is often used between the switches in order to increase the capacity of the connection between them by performing a load balancing of the frames traversing the channel. Load sharing (balancing) is based either on source or destination MAC address of the transmitting computers when layer 2 etherchannel is used. In case of an active link failure (the port in the channel that transmits the frames), the next link is going to transmit the packets with almost no delay. Keep in mind that the word: etherchannel, is a Cisco term. The industry standard name is link aggregation (IEEE 802.3ad).
Enough of the terminology and reasons for using the technology. Let's get practical.
Cisco offers you three ways of configuring the etherchannel ( three modes of operation):
If I decided to use etherchannel in the topology presented in Pic. 1, I could use the following setup using at least two connections between, each forming a single connection like shown below:
For the argument sake I will use a simple network topology below (pic. 3). Now, let's see the configuration options.
Etherchannel using LACP
If you want to configure an etherchannel using a dynamic exchange of packets that is compliant with an industry standard method, the IOS offers you two mode options:
NOTICE!
In case, when both use channel mode passive, the etherchannel will not form since no switch is going to start negotiation.
NOTICE!
It is imperative that you check all the settings of the ports first (all ports must have identical configuration). Candidate ports must be in the shutdownmode. This precaution is used to avoid loops and other issues while establishing the etherchannel.
Etherchannel using PAgP
Port Aggregation Protocol is Cisco proprietory protocol helping establish a virtual link between devices using dynamic negotiation (PAgP frames). Similarly to LACP, it has two modes of operation.
Etherchannel manual
This mode does not exchange any negotiation frames. Be cautious using this method, as switches won't check if port parameters match. Loops can be formed more easily than with the other two methods.
It's time to get our hands dirty!
The configuration assumes that all port parameters are IDENTICAL!
METHOD 1 - LACP (on both switches in my topology shown in pic. 2)
Verification (here on SW1):
METHOD 2 - PAgP (on both switches in my topology shown in pic. 2)
Verification (here on SW1):
METHOD 3 - Manual (on both switches in my topology shown in pic. 2)
Verification (here on SW1):
All configurations that do NOT relate to physical aspects of the ports that are member of the etherchannel must be configured on the port-channel interface now. For instance, if you want to change the channel member ports to a trunk or access mode, the configuration must be done as follows:
I hope this will help you get started. For more information on etherchannel, please refer to Cisco documentation.
In my next post I am going to present switch port security. After that, get ready for layer 3 stuff.
Quick Etherchannel Video Presentation
Layer 2 Etherchannel
When you're designing your network one of the factors you always consider is resiliency. Redundant connections are part of a good design. Consider picture 1 below. A rule of thumb says that if all the devices connected to SW3(access switch on first floor) were transmitting at full speed towards distribution switches (here towards SW1) the traffic is allowed to exceed the capacity of F0/2 port on SW1 20 times. In other words, the link between access layer could oversubscribe 20:1 the link on the distribution switch. Well, it is true in most cases. Remember this is just a rule for an average network.
Pic. 1 - 2-tier network design (access+distribution layer).
Icons designed by: Andrzej Szoblik - http://www.newo.pl
In reality, the situation in which all computers begin to transmit at full speed at the same time never happens. The studies show, that the link between access and distribution switch is utilized in 7% on the average (unless some worm has been planted on your computers). In order to live up to this rule (oversubscription 20:1) you might consider access-to-distribution connection using multiple links that form a virtual connection called: etherchannel. Ports that are members of the etherchannel are represented by a virtual interface called: port-channel.
Etherchannel Advantages
Etherchannel is often used between the switches in order to increase the capacity of the connection between them by performing a load balancing of the frames traversing the channel. Load sharing (balancing) is based either on source or destination MAC address of the transmitting computers when layer 2 etherchannel is used. In case of an active link failure (the port in the channel that transmits the frames), the next link is going to transmit the packets with almost no delay. Keep in mind that the word: etherchannel, is a Cisco term. The industry standard name is link aggregation (IEEE 802.3ad).
Enough of the terminology and reasons for using the technology. Let's get practical.
Cisco offers you three ways of configuring the etherchannel ( three modes of operation):
- Dynamic channel negotiation using Link Aggregation Control Protocol(LACP) which is the industry standard implementation.
- Dynamic channel negotiation using Port Aggregation Protocol (PAgP) which is Cisco proprietary implementation.
- Manual channel configuration without using any form of negotiation.
If I decided to use etherchannel in the topology presented in Pic. 1, I could use the following setup using at least two connections between, each forming a single connection like shown below:
Pic. 2 - Redundant Topology with Etherchannels.
Icons designed by: Andrzej Szoblik - http://www.newo.pl
For the argument sake I will use a simple network topology below (pic. 3). Now, let's see the configuration options.
Pic. 3 - Topology
Etherchannel using LACP
If you want to configure an etherchannel using a dynamic exchange of packets that is compliant with an industry standard method, the IOS offers you two mode options:
- active - in this mode the ports are actively sending negotiation frames to the other switch checking if the required parameters match and the channel can be safely formed.
- passive - in this mode the ports are waiting for the negotiation frames from the other switch in order to form a channel. The ports in the passive mode do NOT initiate any negotiation, but they will reply to negotiation frames received from a neighbor.
- SW1 active - SW2 active
- SW1 active - SW2 passive
- SW1 passive - SW2 active
NOTICE!
In case, when both use channel mode passive, the etherchannel will not form since no switch is going to start negotiation.
NOTICE!
It is imperative that you check all the settings of the ports first (all ports must have identical configuration). Candidate ports must be in the shutdownmode. This precaution is used to avoid loops and other issues while establishing the etherchannel.
Etherchannel using PAgP
Port Aggregation Protocol is Cisco proprietory protocol helping establish a virtual link between devices using dynamic negotiation (PAgP frames). Similarly to LACP, it has two modes of operation.
- desirable - in this mode, ports initiate negotiation frames and check if ports on a neighboring switch have proper settings to establish the etherchannel.
- auto - in this mode, ports cannot initiate negotiation but will respond to the negotiation frames sent by a neighboring switch.
- SW1 desirable - SW2 desirable
- SW1 desirable - SW2 auto
- SW1 auto - SW2 desirable
Etherchannel manual
This mode does not exchange any negotiation frames. Be cautious using this method, as switches won't check if port parameters match. Loops can be formed more easily than with the other two methods.
It's time to get our hands dirty!
The configuration assumes that all port parameters are IDENTICAL!
METHOD 1 - LACP (on both switches in my topology shown in pic. 2)
SW(config)#interface range f0/13 - 14
SW(config-if-range)#channel-group 1 mode active
SW(config-if-range)#end
SW#
Verification (here on SW1):
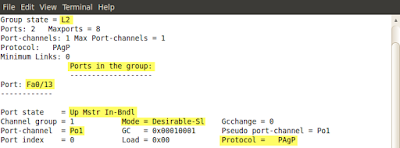
Pic. 4 - "show etherchannel summary" command.
Pic. 5 - "show etherchannel 1 detail" command.
In the above picture (pic. 5), part of the output has been truncated for a clarity.
METHOD 2 - PAgP (on both switches in my topology shown in pic. 2)
SW(config)#interface range f0/13 - 14
SW(config-if-range)#channel-group 1 mode desirable
SW(config-if-range)#end
SW#
Verification (here on SW1):
Pic. 6 - "show etherchannel summary" command.
Pic. 7 - "show etherchannel 1 detail" output.
In the above picture (pic. 7), part of the output has been truncated for a clarity.
METHOD 3 - Manual (on both switches in my topology shown in pic. 2)
SW(config)#interface range f0/13 - 14
SW(config-if-range)#channel-group 1 mode on
SW(config-if-range)#end
SW#
Verification (here on SW1):
Pic. 8 - "show etherchannel summary" command.
Pic. 9 - "show etherchannel 1 detail" command.
In the above picture (pic. 9), part of the output has been truncated for a clarity.
All configurations that do NOT relate to physical aspects of the ports that are member of the etherchannel must be configured on the port-channel interface now. For instance, if you want to change the channel member ports to a trunk or access mode, the configuration must be done as follows:
SW(config)#interface port-channel 1
SW(config-if)#switchport trunk encapsulation dot1q
SW(config-if)#switchport mode trunk
I hope this will help you get started. For more information on etherchannel, please refer to Cisco documentation.
In my next post I am going to present switch port security. After that, get ready for layer 3 stuff.
Quick Etherchannel Video Presentation










Comments
Post a Comment